Hello folks. After building some sites with the new DNN Azure AD B2C provider, some new features have been being added over the last months, so is time to package them into a new release. I’m excited to announce the v1.2 release of the B2C provider, with solutions for some interesting scenarios. All the code is available at GitHub, and here is the link to the release notes:
Release notes
New features
- Added support for multiple-portals scenario:
- Added a new "Use Global Settings" setting to allow all portals on the same instance to share the configuration settings and use the same B2C tenant
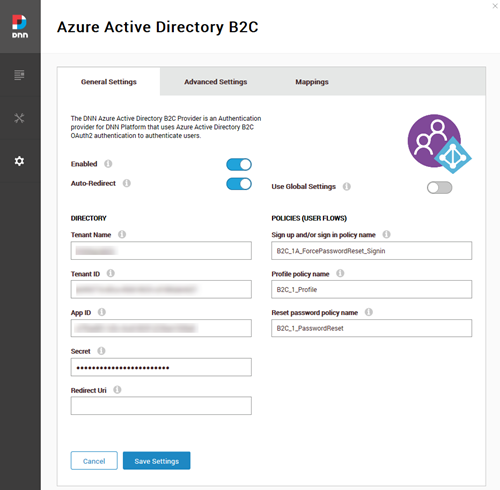
- Added a new "Redirect Uri" setting to allow customization of the redirection after a user login
- Added a Redirection Controller to handle the user redirection on multi-portal auth scenario
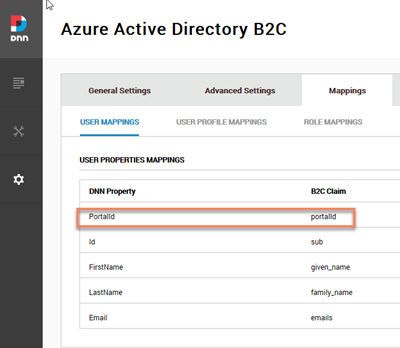
- Added support for the special user claim mapping "portalId", to use it as a filter per portal.
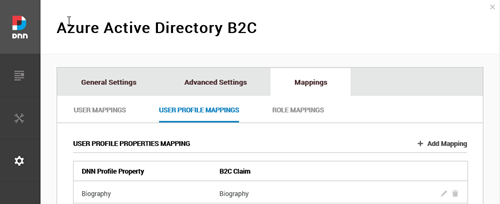
- Added new support for custom claim mappings: user mappings, user profile mappings and role mappings. All the mappings are stored on the database and can be customized per portal.
- New user management module allows to manage Azure AD B2C users directly from the DNN interface, including the force password reset attribute (check "Samples/CustomPolicies/SignInWithForcePasswordReset").
- Now the user and role prefix can be disabled, so user and role names are more friendly (works really well when using "emails" claim as "Id" on the User mappings).
- When using JWT auth, now the user is synced in the same way than when using the web UI, even if the user doesn't exist (the user is then created and synced).
- Added Spanish (human) and German (auto) localizations.
Fixes
- Cache is now correctly cleared out after a configuration change
- User cache is correctly cleared out after a login, so the sync is done correctly
- Other bug fixes
List of contributors
Noteworthy Changes in v1.2
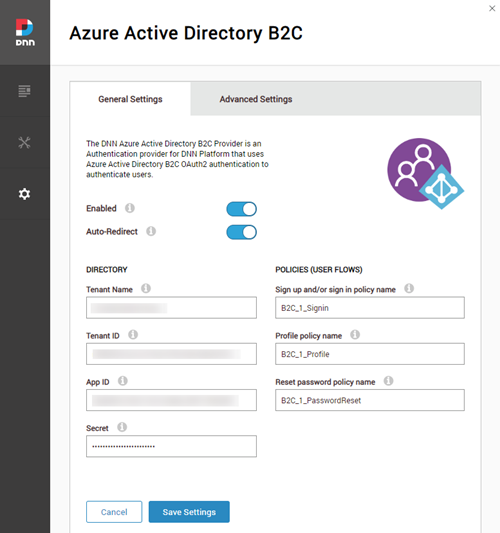
Claim and role mappings by portal
This is one of the biggest changes on this version, allowing to map not only the user profile attributes, but also the user properties (username, Firstname, Lastname, email and portalId) as well as mapping the role synchronization (map a B2C role with an existing DNN role). Note that when using claim mappings, you can use custom attributes by adding the “extension_” prefix to the claim value (i.e. “extension_LoyaltyNumber”).
In this version, all the mappings are now stored on the DNN database and can be setup per portal.
Multi-portal support
The provider now supports working with multiple portals and sharing the same Azure AD B2C scenario with the introduction of some new settings to simplify the maintenance and make it possible. The first important setting is the “Use Global Settings”, so when this setting is set, all the provider settings are stored at host level instead of per portal (even the claim mappings).
A special mention to the “Redirection Controller” with the endpoint https://mysite.com/api/DotNetNuke.Authentication.Azure.B2C.Services/Authorization/RedirectToPortal built for this scenario, and successfully redirecting the user to the right portal when the B2C tenant is being shared across the DNN instance.
To take advantage of the new multi-portal support, you just need to setup two things:
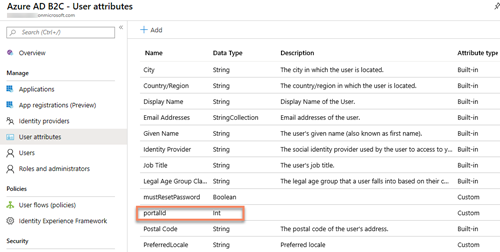
- Create a custom attribute called “portalId” of type “Integer” on the B2C tenant
- Setup the “portalId” user mapping
Then you optionally can use the two new settings mentioned on the previous paragraphs to make the whole configuration easier.
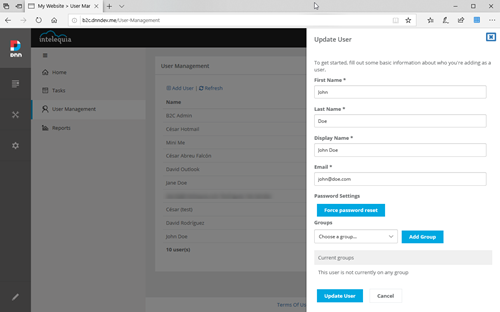
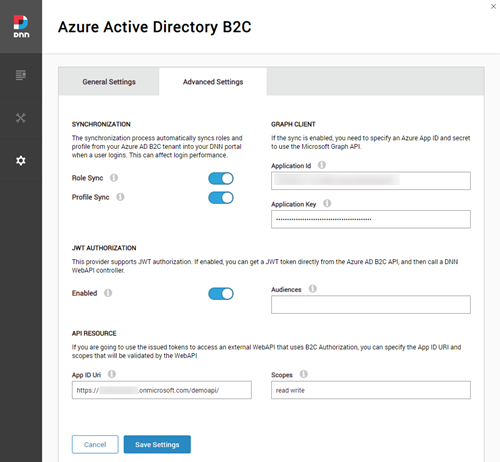
New User Management Module
There is a new user management module that allows to manage the B2C users directly from the DNN user interface. The module uses the MS Graph API under the hoods, so the advanced settings must be setup before using the module. Operations allowed on this version are: CRUD user operations (including specifying auto-generated or manually entered passwords), sending a welcome e-mail, modifying the role membership and force the password on the next logon.
To allow the “Force password reset” command to work, a B2C custom policy must be setup. The steps would be:
- Create a custom attribute called “mustResetPassword” of type “Boolean” on the B2C tenant
- Follow the setup instructions described at https://github.com/intelequia/dnn.azureadb2cprovider/tree/master/samples/CustomPolicies/SignInWithForcePasswordReset/LocalAccounts
Give it a try and if you found any issue, please fill an issue on GitHub! Pull requests are welcomed!




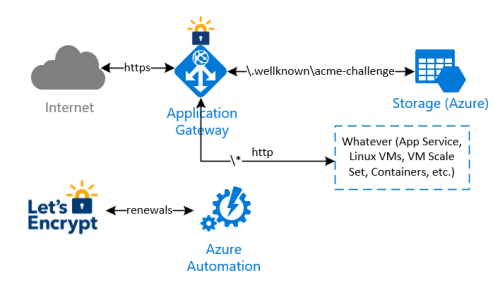
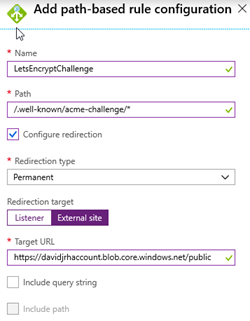
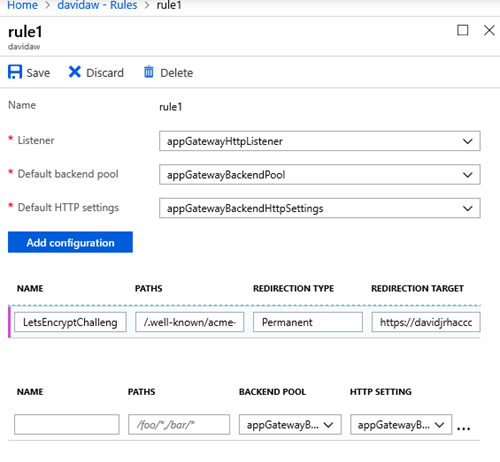
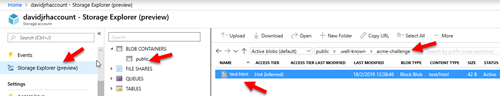
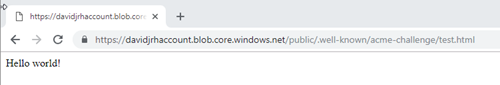
 Let’s Encrypt
Let’s Encrypt